Classification of Identity Management Approaches
Reviewed by Greg Wilson / 2023-03-30
Keywords: Security
It's hard to make progress without discussing things, and it's hard to discuss things if you don't agree on terminology. This paper presents a systematic, comprehensible classification of various approaches to identity management, and gives examples (like the two shown below) of where different use cases fit. By creating this, the authors have made it easier for us to see where we agree and disagree, and have also pointed out some interesting gaps in existing approaches. There are (necessarily) a lot of acronyms in the paper, but anyone implementing identity management should read it, and it would be a great starting point for a lecture or two in an undergrad course on system design or software architecture.
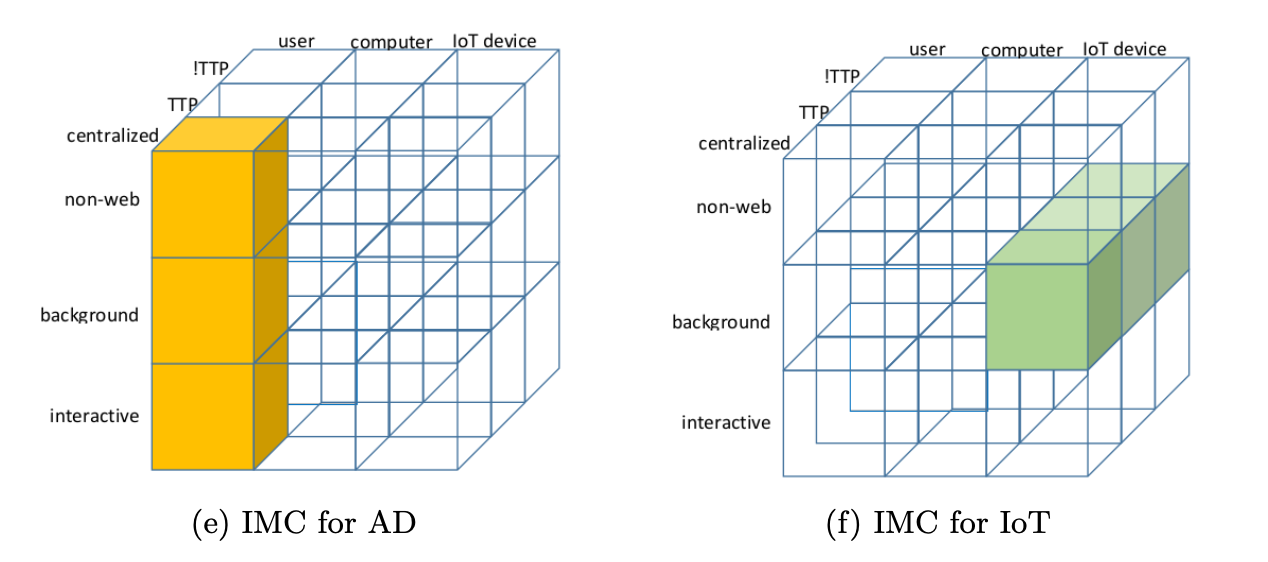
Daniela Pöhn and Wolfgang Hommel. IMC: a classification of identity management approaches. 2023. arXiv:2301.00444.
This paper presents a comprehensive classification of identity management approaches. The classification makes use of three axes: topology, type of user, and type of environment. The analysis of existing approaches using the resulting identity management cube (IMC) highlights the trade-off between user control and trust in attributes. A comparative analysis of IMC and established models identifies missing links between the approaches. The IMC is extended by a morphology of identity management, describing characteristics of cooperation. The morphology is then mapped to the life cycle of users and identity management in a further step. These classifications are practically underlined with current approaches. Both methods combined provide a comprehensive characterization of identity management approaches. The methods help to choose suited approaches and implement needed tools.